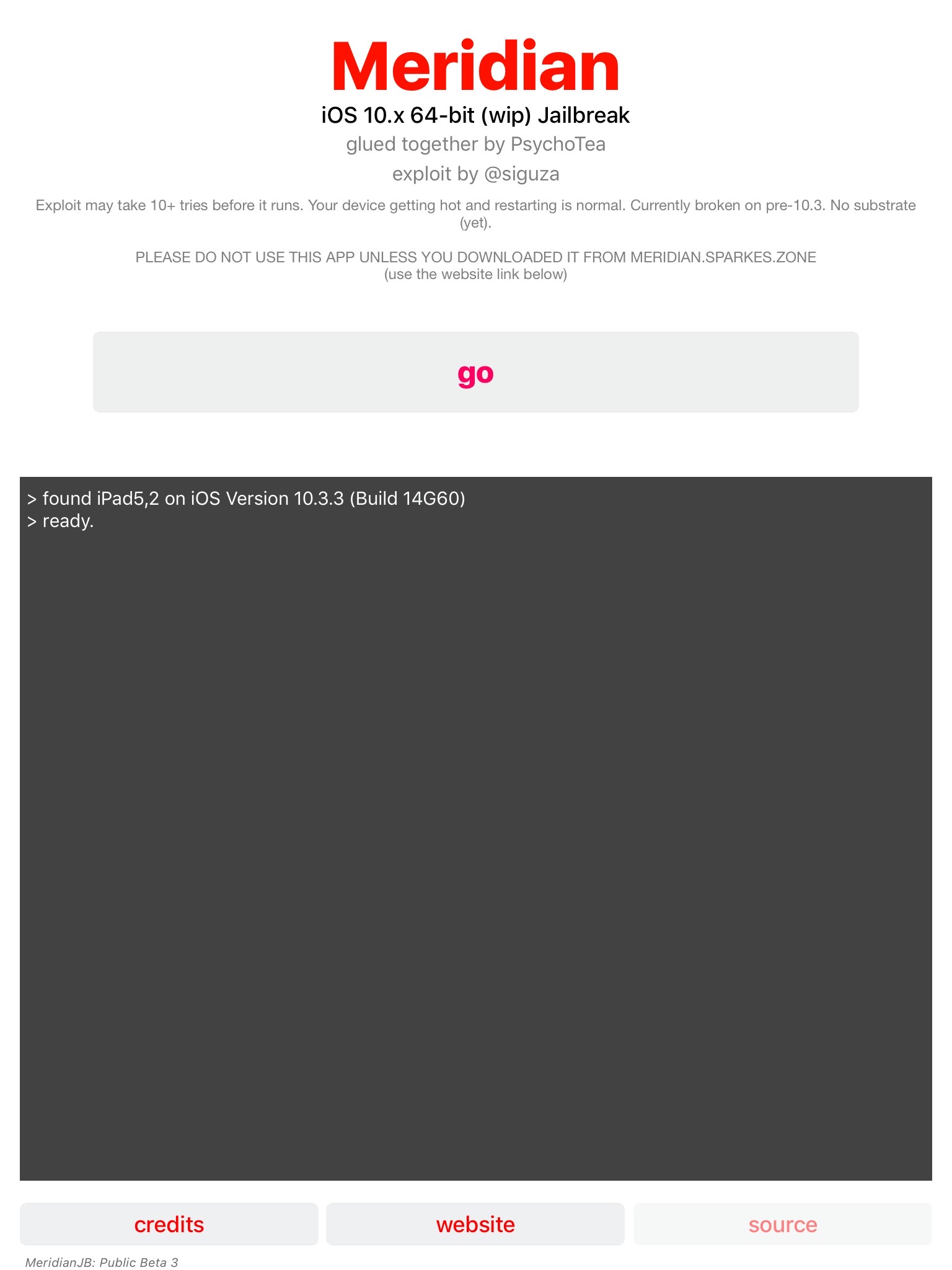
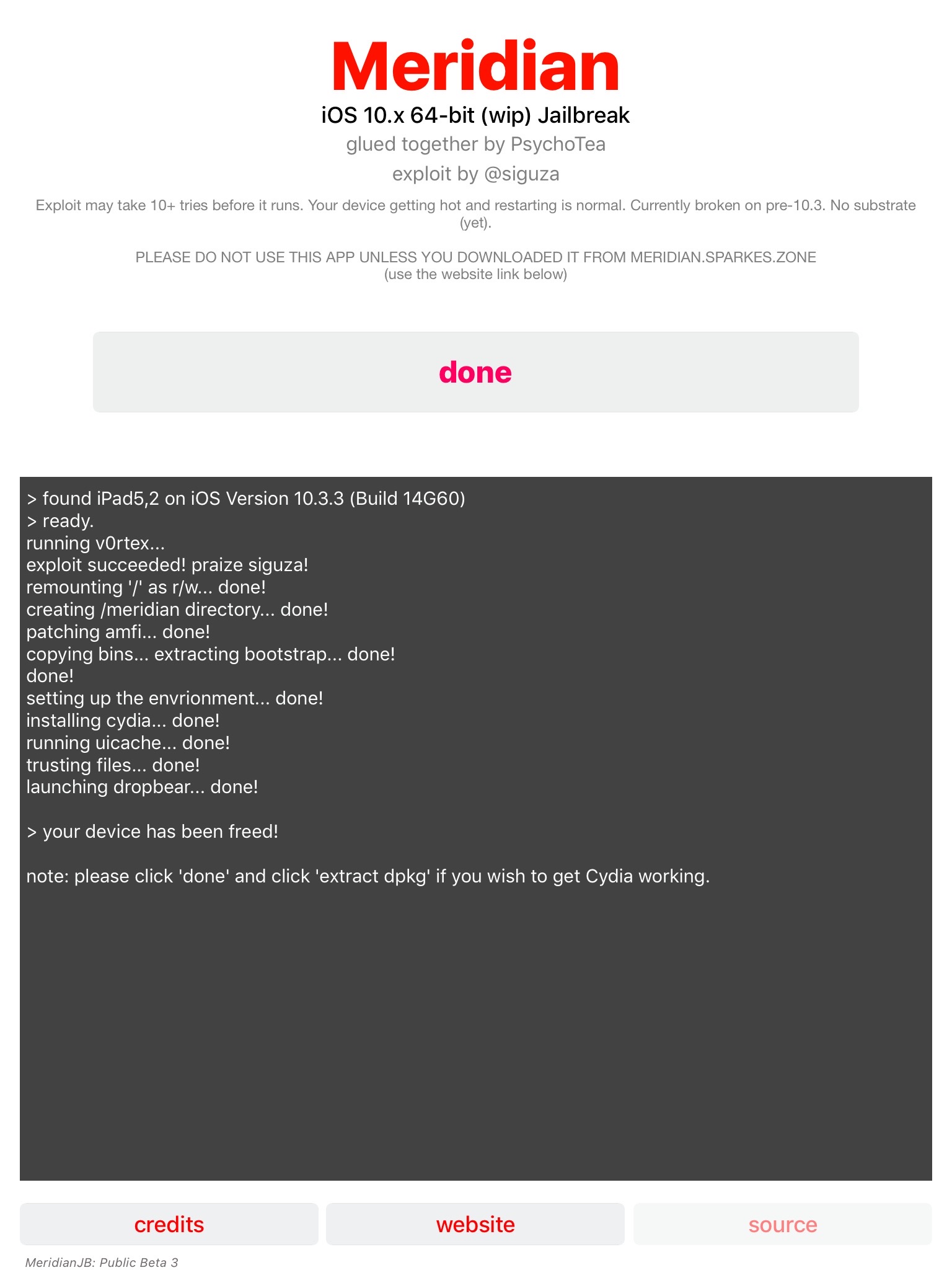
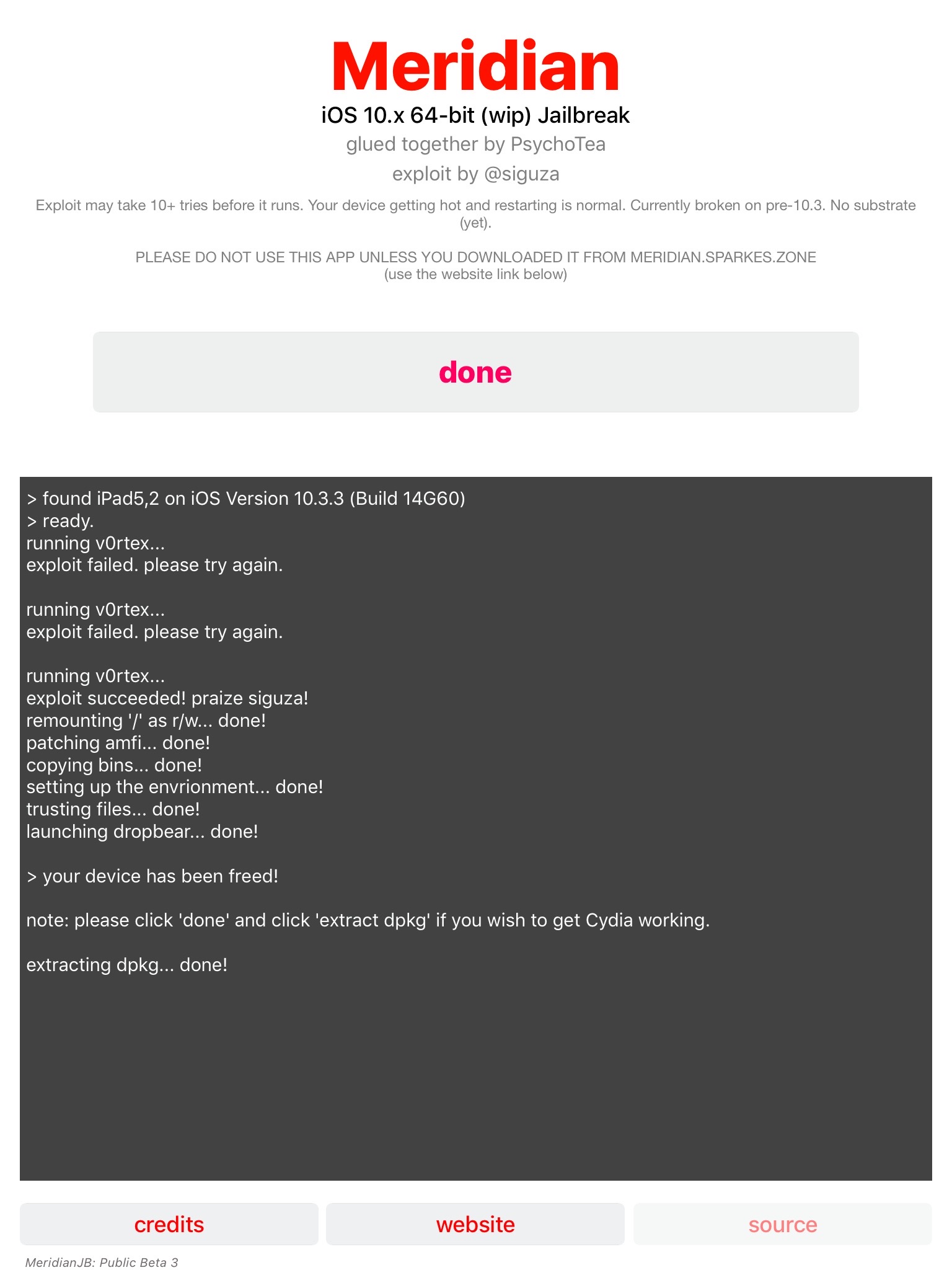
Next step is to SSH into the device. This was also a bit frustrating – part of it because I didn’t read the FAQ and part because the SSH software installed on the device is not very stable.
First off the SSH port used is on 2222, not the normal 22 so be aware of that if you use iproxy like myself – you need to use the command ‘iproxy 2222 4242 (or some other port number) instead of ‘iproxy 22 2222’.
Second is the SSH software used, dropbear. I had serious issues attempting to SSH into this device. Sometimes it worked, sometimes it refused the connection. Just keep trying is my solution – it will eventually work.
Finally, once you are in be sure to change the passwords for the ‘root’ and ‘mobile’ accounts by using the command ‘passwd root’ and ‘passwd mobile’ (see the screen shot below in the next section).
To image the device you can use a modified version of the command that I used in my previous blog article (assuming you are using iproxy for USB tethering – modify as needed if not).
ssh –p 4242 root@127.0.0.1 '/meridian/bins/tar –cf - /' > ios_physical_logical_dump.tar
This jailbreak (as well as LiberiOS) are installing their own set of binaries which include some normal Unix utilities not installed on iOS. The tar command is in a different directory than what is normally used therefore it may not work to just use ‘tar’, instead point it to the one Meridian put on the device.
Another item you may have noticed that has changed with the command above is that I’m doing a ‘physical logical’ acquisition of the entire device using from the root directory or ‘/’. Previously I would capture the system partition as a full dd image using /dev/disk0s1s1, however something with these newer operating systems is limiting my access to it. Best guess at this point is that it’s an APFS thing ¯\_(ツ)_/¯ . Shown below doing a simple 'xxd' to view the partition is not permitted as root, this also goes for 'dd' and other utilities.